Today’s authentication state of the art uses two of a few possible factors identify us. We call this Two-factor authentication (2FA). The possible factors include:
- Something you know – for example, a password.
- Something you have – maybe a cell phone or one-time-password (OTP) generator.
- Something you are – biometrics such as fingerprints, eyeballs, voices, or faces.
A couple of others also sometimes see action.
- Somewhere you are – such as an IP Address on the internet.
- Something you do – such as specific hand gesture.
2FA usually uses something we know combined with something we have. We use 2FA all the time when we enter a password to log into a website and the website sends a cell phone text message with a one-time-code. This isn’t a perfect 2FA implementation, but better than the old days with just a password.
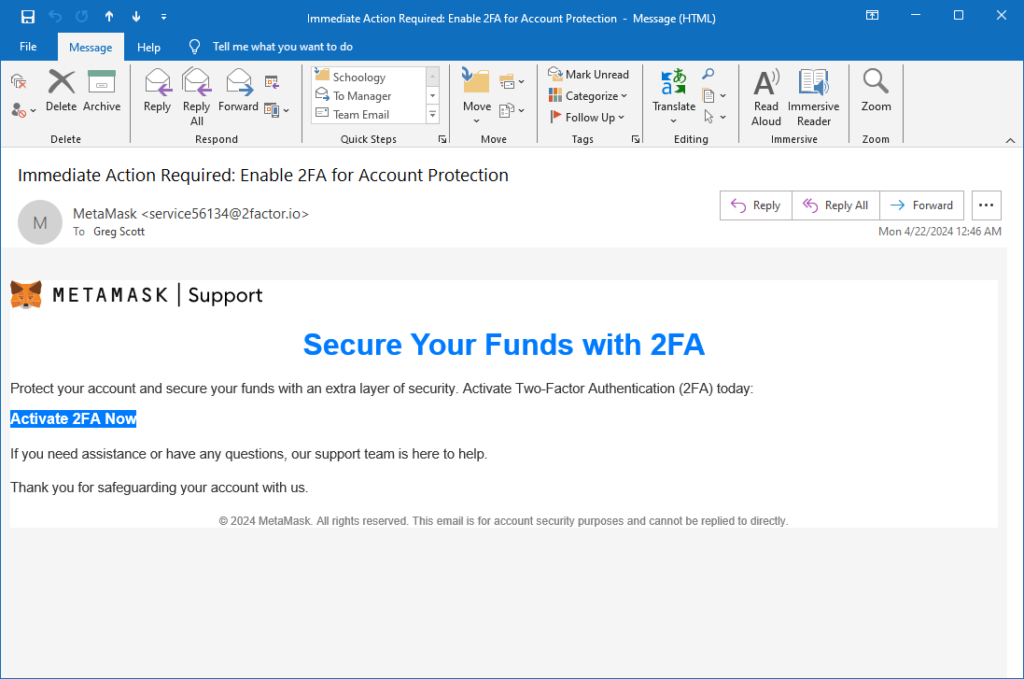
A clever attacker registered a domain name to look similar to Facebook’s parent, Meta, and then sent out this email enticing gullible people to follow a link. The email claims to come from a domain name named 2factor.io, which looks reasonable. But the “Activate 2FA now” link goes to a Russian website named https://human-captcha.ru.
Don’t go there.
This will fool gullible people who want to do the right thing. But it won’t fool you. Don’t phall for phishing. I’ll give this one a B+.
For more phishing samples, see my phish collection.

Thank you!!
You’re welcome!