The very first thing I learned about cybersecurity was, learn to think like an attacker. And since online grooming is a cybersecurity problem, if I want to to understand how today’s traffickers find online grooming victims, then I need to think like a trafficker. Maybe this will lead to useful defense tactics.
Back in 2019, while researching “Trafficking U,” I searched for a reformed trafficker willing to talk to me. I found John Turnipseed. He was a notorious Minneapolis gang leader, pimp, and drug dealer until 1994, when he turned his life around and accepted Jesus. He became one of the first participants in Urban Ventures’ Center for Fathering, eventually running the center. Later, he served as Urban Ventures’ Executive Vice President and Campus Pastor. He mentored hundreds of men to become better fathers before meeting the Lord on Nov. 22, 2022.
John told me that when he was pimping, he found women to work for him by charming them, learning what they wanted, and offering it. They all were vulnerable because of issues with their fathers, and they always wanted another father figure. John said pimps are masters at exploiting that vulnerability. That was why he worked tirelessly at Urban Venture’s Center for Fathering after he put his life together.
John said that in his day, grooming was face to face and personal. Today, online grooming happens over the internet. It’s still personal, but potential victim social media profiles often advertise vulnerabilities to traffickers. And traffickers use fake social media profiles to lure them in.
Probing Wide for Online Grooming Victims
Traditional cyberattackers first probe wide across the internet, looking for potential victims who might be vulnerable, and then they probe deep when they find one. Today’s traffickers probably do the same thing by probing public social media posts and starting private dialogs with potential victims. That’s how a trafficker found a fifteen-year-old victim in Paul Boge’s nonfiction book, “The True Story of Canadian Human Trafficking.” In my newest novel, “Trafficking U,” Jesse Jonsen tries to lure a trafficker with a fake social media profile and reverse-grooming.
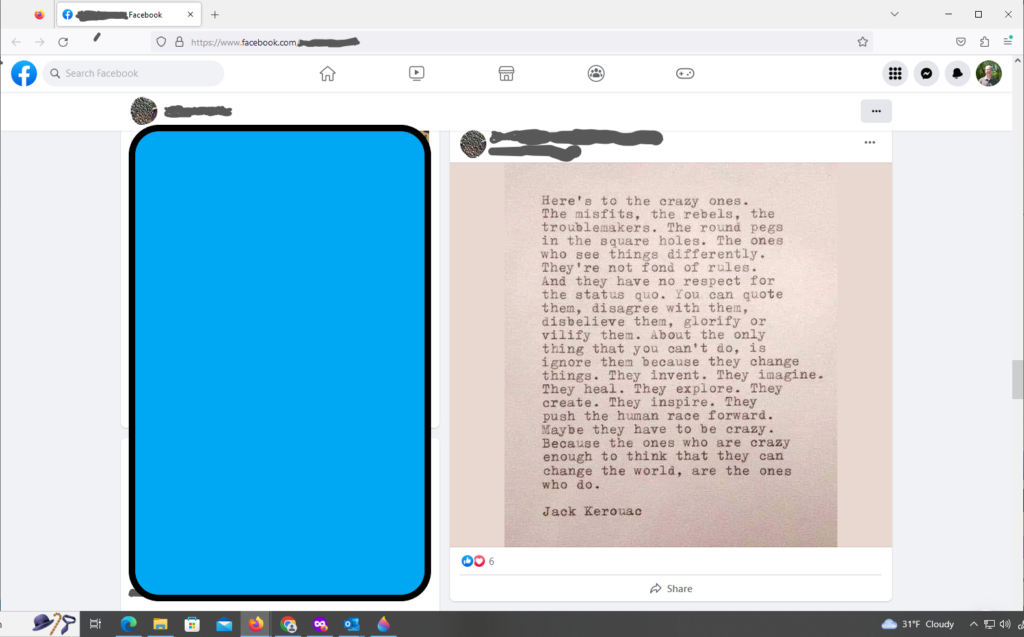
And, so I probed Facebook, looking for somebody who might be vulnerable. It took around five minutes to find Alice’s profile. Alice is not her real name. She posted an image with a quote celebrating misfits and rebels and it caught my eye.
Put her in the pipeline.
Probing Deep for Slaves
The rest of this blog post is hypothetical. Just like with traditional cybersecurity, thinking like an attacker does not mean actually mounting an attack.
As a trafficker, I need to be both visible and hidden. That’s why I would use a fake social media profile. From there, I would reach out to Alice, maybe with an innocent public comment about her post, and maybe also with a private message. I would start by telling her how much I love her quote and ask her why she posted it. I would look for common ground. Hey, I can play a misfit role. Maybe I would reference the movie, A Bug’s Life and the character, Flik, also a misfit full of better ideas.
We would trade lots of messages and I would gain her trust. Just a fellow misfit working through life the best he can.
And then I would suggest video. Why not? We like each other. Might be fun. Of course she would say yes, and now we would talk face to face over the internet. Two misfits navigating a hostile world that doesn’t understand us. It would be our secret.
When the timing is right, I would ask her address. Why? Well, because, um, well, I like you and I want to send you a present. Nothing big, maybe a Flik doll or something silly to show how much a fellow misfit cares for you.
Maybe I would take her to dinner. Somewhere nice, maybe just a little bit edgy. We might go on lots of dates. Maybe we’ll go to movies, or the zoo, or the state fair, or anywhere else she likes. If you live with your parents, just tell them you’re out with friends. They’ll never understand our special bond. Or sneak away. I’ll pick you up somewhere and drop you off and they’ll never know you were gone. Another special secret.
By now, I’m months into this recruiting project. I need an return on my investment.
Time to Strike
Wanna pose for some pictures? C’mon, it’ll be fun. Besides, you’re beautiful. Why not show it off? And let’s show those pictures to a few people. Do you have any idea how much money people will pay for access to that beauty? You are so special. Let’s build a future together.
But really, you’ll be my slave. Of course, you can leave any time you want. But why are you so ungrateful? Why do you hurt me all the time when I work so hard to take care of you? Your parents disowned you, your friends abandoned you, and everyone hates you because of the terrible things you do. I know all your secrets, but I’m the only person in the world who still cares about you. I’m all you have. Without me, you’re dead. Or worse. Never forget that.
And the longer you stay with me, the more I’ll rewire your brain. Until you’re not useful to me anymore and I toss you aside. Because you’re really just a tool of production and when you stop making money for me, I’ll start the cycle again with somebody else.
Online Grooming – Where technology and psychology meet.
Criminals are often technology pioneers. If I were a trafficking kingpin, I would want to grow my operation because bigger means more money, and if I don’t do it, somebody else will. But probing and grooming are labor-intensive. Maybe I would automate it using an AI model trained to find people who advertise vulnerabilities. The AI model would handle social media dialog by offering the right messages to ensnare potential slaves. For the video phase, maybe I would use deep fake videos to show a virtual me and mate it with my AI model for dialog to reinforce my messaging. Anyone who passes through that process would meet the real me. And I would own them.
Welcome to high-tech slavery. This is the creepiest attack I’ve ever envisioned.

Wow. So dark and sinister. I hope your words make it to the ears that should hear them.
Thanks. Tell everyone you know about this blog post. And let’s create demand for “Traffic School” so we attract a publisher’s attention with deep marketing pockets.
Oh wow…. I had to post this on my Facebook to let others know. Thank you for sharing your skills.
and know please know this is just a dip and a taste of how people out there are actively and very deceptively seeking to exploit and use children for personal and trafficking abuse. The people out there, real traffickers play the long game, rarely do they snatch someone’s child off the street, rarely is it the creeper in a van. These people will work to build a relationship with your child, or with whomever they are trying to exploit.. they will take their time and it can take months many months before they actually physically get hands on that child… and they can exploit and trafficked that child while they still live at home and you may never know.