I had heard about different DDoS attacks, including SYN flood attacks, for a long time. In fact, I got serious about cybersecurity in November, 2000 after I found my internet-facing DNS server an unwitting part a DDoS attack against the government of Brazil.
In a DDoS (Distributed Denial of Service) attack, somebody orchestrates lots of systems to flood a victim with traffic, denying internet service to the victim. One popular attack is called a SYN flood.
On Friday, October 11, 2024, somebody hit me with a SYN flood attack. Full circle – my attacker was from Brazil. I’m not sure if I should be honored or irritated. Maybe both. But I’m getting ahead of myself.
(This turned out to be wrong. My attacker was not from Brazil. Brazil was even more of a victim than me. We share a common enemy. See, “My DDoS attack: the rest of the story,” for more.)
I had noticed internet hiccups the prior few days. Connecting to our TV streaming services was slow. Max Headroom moments interrupted a few video meetings. Sometimes Google video meetings just dropped. Every interaction with the internet just felt slow. So I finally decided to look into it.
Define the problem
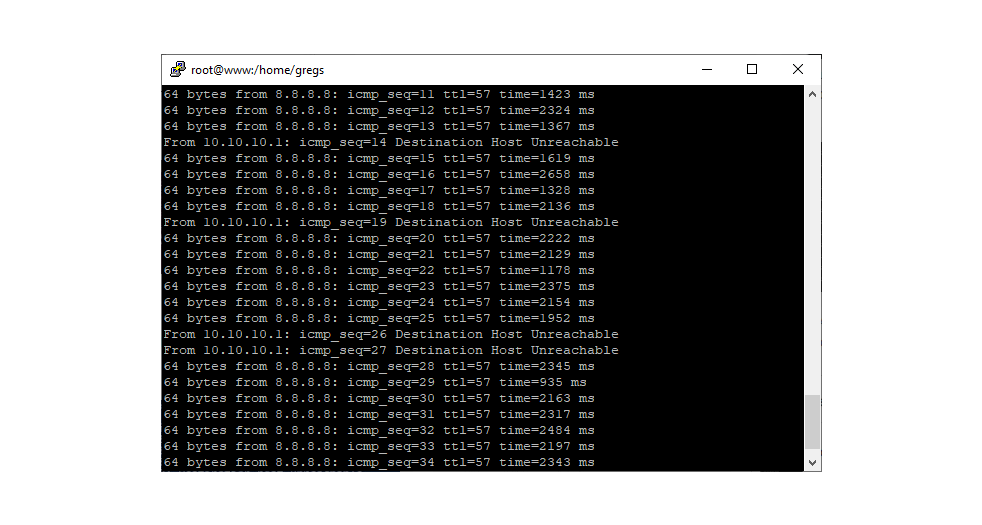
Google offers a quick and dirty diagnostic service by allowing the world to ping its DNS server at IP Address 8.8.8.8. I tried it. Results were similar to the simulated output in the screen shot at the top of this blog post. Round trip times to Google with my internet service should be between ten and fifteen milliseconds. The round trip times of 2+ full seconds I saw are around 100 times slower than normal, or like comparing an airplane trip to walking. Something was wrong. Time to dig deeper.
I spent more than twenty years building firewalls for a living. I still use one of my Red Hat Fedora Linux firewalls at my own boundary because Linux offers a wealth of network diagnostic tools and all the commercial firewall/routers use Linux at their core. Traceroute, borrowed from the older Unix world, uses ICMP packets to show users the route to any destination on the internet. It’s kind of like tracing the path from New York to Los Angles on a physical map. I used traceroute to find the telco router closest to me and then pinged it from a Windows system. Results were ugly.
...
Reply from 207.109.2.10: bytes=32 time=780ms TTL=253
Reply from 207.109.2.10: bytes=32 time=915ms TTL=253
Reply from 207.109.2.10: bytes=32 time=886ms TTL=253
Reply from 207.109.2.10: bytes=32 time=720ms TTL=253
Request timed out.
Request timed out.
Reply from 207.109.2.10: bytes=32 time=1209ms TTL=253
Reply from 207.109.2.10: bytes=32 time=1065ms TTL=253
Reply from 207.109.2.10: bytes=32 time=731ms TTL=253
Request timed out.
Ping statistics for 207.109.2.10:
Packets: Sent = 100, Received = 74, Lost = 26 (26% loss),
Approximate round trip times in milli-seconds:
Minimum = 515ms, Maximum = 2787ms, Average = 1084ms
C:\Users\gregs>Round trip times should have averaged around 5 milliseconds, not 1000+ milliseconds. This also showed the problem was between my internet provider and me, not some routing problem on the internet.
Dig deeper
Over the years, I’ve seen service issues with flaky telco equipment. One time, I fought a partial outage for months until I finally convinced my internet service provider that the problem was a router in its infrastructure. Another time, I drove my car to a central office and banged on the door until somebody answered and addressed my problem. I recently replaced my old Centurylink fiber modem after my old one showed too many service problems. Maybe this was another telco equipment issue.
But what if something was going on I didn’t know about? I tried another Linux tool named iptraf-ng to get a feel for how much traffic flew in an out. I should have captured a screenshot.
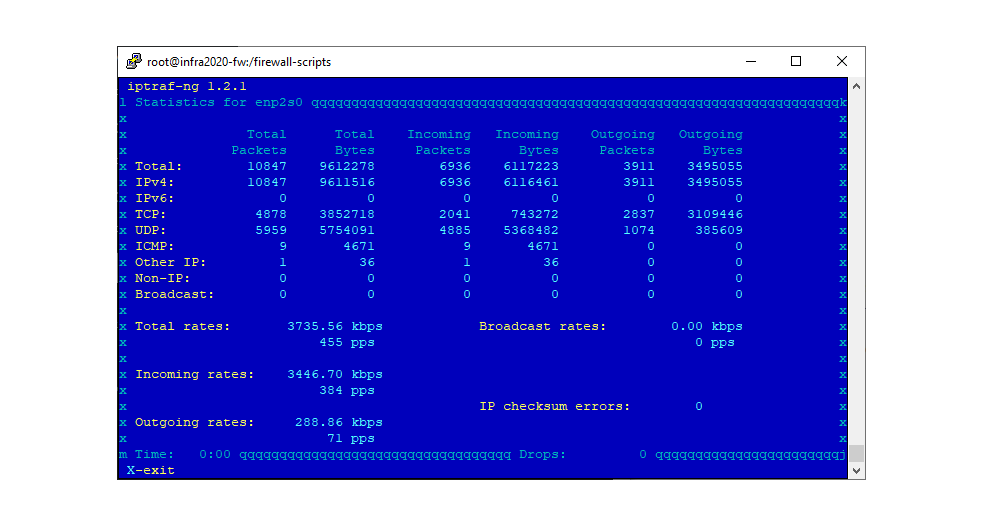
I took this screenshot while composing this blog post. It shows around 3.447 megabits of traffic coming in, and around 289 kilobits going out. During the attack, that incoming rate spiked at closer to 30 megabits per second. On a network that should have been mostly idle. Something ugly was definitely going on.
Where did all that traffic come from? I used a tool named tcpdump to find out. Here is a snippet showing one of millions of network packets flying in.
18:40:46.343734 IP 187.111.194.242.51283 > 216.160.2.132.443: Flags [S], seq 2127035781, win 64240, options [mss 1460,nop,wscale 8,nop,nop,sackOK], length 0My Microsoft Exchange email server advertises a secure website at public IP Address 216.160.2.132 for remote email. Secure websites use TCP port 443. An attacker from IP Address 187.111.192.242, and others in that range, flooded it, millions and millions of times.
Who is this clown?
The Linux whois tool told me my attacker was from Brazil.
[root@infra2020-fw ~]# whois 187.111.192.197
[Querying whois.lacnic.net]
[Redirected to whois.registro.br]
[Querying whois.registro.br]
[whois.registro.br]
% Copyright (c) Nic.br
% The use of the data below is only permitted as described in
% full by the Use and Privacy Policy at https://registro.br/upp ,
% being prohibited its distribution, commercialization or
% reproduction, in particular, to use it for advertising or
% any similar purpose.
% 2024-10-11T21:08:38-03:00 - IP: 216.160.2.129
inetnum: 187.111.192.0/20
aut-num: AS53123
abuse-c: PTLME5
owner: Power Telecomunicações Ltda. - ME
ownerid: 07.802.639/0001-30
responsible: João Paulo Pessoa Guimarães
country: BR
owner-c: PTLME5
tech-c: PTLME5
created: 20100128
changed: 20240221
nic-hdl-br: PTLME5
person: Power Telecomunicações Ltda ME.
e-mail: noc@powertelecom.net.br
country: BR
created: 20090914
changed: 20240118
% Security and mail abuse issues should also be addressed to
% cert.br, http://www.cert.br/ , respectivelly to cert@cert.br
% and mail-abuse@cert.br
%
% whois.registro.br accepts only direct match queries. Types
% of queries are: domain (.br), registrant (tax ID), ticket,
% provider, CIDR block, IP and ASN.
[root@infra2020-fw ~]#
SYN Flood DDoS attack
Similar to when people strike up conversations, computers use a three-way handshake to start computer to computer TCP conversations. If a computer named Alice wants to start a TCP conversation with a computer named Bob, Alice sends Bob a packet with the SYN bit set. If Bob wants to talk to Alice, then Bob responds with a packet with SYN and ACK bits set. Alice finishes the handshake with an ACK packet. And now, Alice and Bob trade messages.
Sometimes, attackers exploit that three-way handshake by flooding a victim with SYN packets. If attackers can overwhelm the victim, then the victim can no longer interact with the internet because it’s tied up handling that flood of SYN packets. This denies service to the victim.
And somebody from Brazil was doing it to me. I confirmed it from my email server. Count the 337 SYN_RECEIVED packets in the Windows netstat output below from lots of IP Addresses in the range from the whois output above.
Microsoft Windows [Version 10.0.17763.6189]
(c) 2018 Microsoft Corporation. All rights reserved.
C:\Users\administrator.INFRASUPPORT>netstat -an
Active Connections
Proto Local Address Foreign Address State
TCP 0.0.0.0:21 0.0.0.0:0 LISTENING
TCP 0.0.0.0:25 0.0.0.0:0 LISTENING
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING
TCP 0.0.0.0:81 0.0.0.0:0 LISTENING
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING
TCP 0.0.0.0:443 0.0.0.0:0 LISTENING
.
.
.
TCP 0.0.0.0:64337 0.0.0.0:0 LISTENING
TCP 10.10.10.12:139 0.0.0.0:0 LISTENING
TCP 10.10.10.12:443 10.10.10.1:50009 ESTABLISHED
TCP 10.10.10.12:443 10.10.10.1:51928 ESTABLISHED
TCP 10.10.10.12:443 10.10.10.1:56048 ESTABLISHED
TCP 10.10.10.12:443 10.10.10.140:58058 ESTABLISHED
TCP 10.10.10.12:443 10.10.10.140:58074 ESTABLISHED
TCP 10.10.10.12:443 187.111.192.32:41981 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.192.34:1784 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.192.48:9423 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.192.89:32895 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.192.114:24619 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.192.130:42961 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.192.136:36083 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.192.139:43698 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.192.169:16383 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.192.169:60162 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.192.190:37439 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.192.195:35929 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.192.206:11645 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.192.220:2525 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.192.224:25035 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.192.228:33917 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.6:54731 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.7:32955 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.12:28597 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.38:39776 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.45:36119 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.46:37257 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.90:65381 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.102:53039 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.110:59609 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.124:20365 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.130:37792 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.143:37868 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.176:54255 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.180:42281 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.182:36576 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.190:21831 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.194:37074 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.225:54799 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.236:48512 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.193.253:23474 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.22:6147 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.39:30721 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.87:25552 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.98:21336 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.98:63566 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.106:59104 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.114:37983 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.119:186 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.121:50948 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.126:54775 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.165:25013 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.166:26933 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.178:35563 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.183:7440 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.183:9028 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.199:11033 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.235:64567 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.236:64562 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.194.237:41708 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.4:59601 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.19:10735 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.22:15913 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.37:36793 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.52:9176 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.63:15526 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.73:41907 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.79:38879 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.104:42673 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.106:36135 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.111:4734 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.120:54078 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.129:52559 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.130:56417 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.134:24119 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.143:64495 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.156:43148 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.169:42091 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.181:3728 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.226:15304 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.232:42859 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.235:53540 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.237:30936 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.240:65050 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.195.243:25877 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.15:4684 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.16:17000 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.16:47009 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.23:55639 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.51:24996 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.66:21430 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.71:24313 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.79:4732 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.79:37656 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.81:35754 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.91:18207 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.106:3947 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.122:25142 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.140:44290 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.173:32104 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.173:61566 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.194:29477 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.198:36727 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.205:17108 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.208:2346 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.212:25005 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.213:10488 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.235:22534 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.238:14620 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.196.247:19843 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.197.10:29293 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.197.20:46676 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.197.40:6031 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.197.46:1461 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.197.63:30988 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.197.102:2773 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.197.109:22533 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.197.146:16151 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.197.180:65329 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.197.225:37657 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.197.240:40347 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.197.241:29745 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.197.242:45728 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.197.253:60833 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.0:20091 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.28:26611 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.77:12675 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.87:52123 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.98:39660 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.104:45122 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.119:13596 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.123:2478 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.134:48494 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.147:44818 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.149:59405 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.157:60398 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.158:44991 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.163:23886 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.169:31401 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.174:64800 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.204:41846 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.213:6640 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.232:5561 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.246:54917 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.198.251:57456 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.199.27:54083 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.199.47:19395 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.199.61:36523 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.199.93:22722 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.199.119:61604 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.199.138:15678 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.199.140:59862 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.199.155:20378 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.199.164:9429 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.199.169:47909 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.199.197:51794 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.199.202:12421 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.199.206:57266 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.199.214:8327 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.15:640 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.22:16815 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.111:19962 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.123:15199 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.128:477 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.137:21907 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.150:61378 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.154:33405 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.156:4524 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.167:63732 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.169:5544 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.169:54078 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.186:15225 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.200:61533 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.214:57948 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.220:33350 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.228:12030 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.232:15165 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.239:31489 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.200.251:29055 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.24:27536 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.44:35181 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.50:21999 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.70:47606 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.79:42863 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.82:11460 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.84:21334 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.93:60759 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.97:11904 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.107:1264 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.111:16504 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.129:58764 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.131:48316 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.154:29027 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.186:62775 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.188:14409 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.202:62465 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.214:13721 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.221:21543 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.229:3841 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.201.233:1469 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.12:34938 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.27:8267 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.36:61341 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.40:45496 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.43:55330 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.45:14135 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.53:63226 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.79:4224 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.89:38882 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.135:50582 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.146:1901 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.149:20069 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.164:39886 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.171:27611 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.178:61855 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.195:12506 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.199:29548 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.201:45119 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.207:36223 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.215:62555 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.216:8850 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.202.219:10272 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.0:55732 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.8:19726 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.24:9850 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.51:30377 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.61:25993 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.61:48549 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.63:31113 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.64:39562 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.71:48315 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.76:19574 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.95:22914 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.135:48135 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.148:35640 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.150:10545 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.168:5916 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.171:52412 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.172:2223 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.175:3648 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.184:42875 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.201:64206 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.229:62034 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.232:4776 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.203.237:13872 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.7:19272 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.8:61699 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.24:27300 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.47:49403 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.66:6451 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.66:43044 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.80:6471 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.80:29436 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.96:8360 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.100:38070 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.111:19590 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.111:42726 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.116:30422 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.121:41480 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.128:33671 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.134:56527 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.138:47313 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.144:3605 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.156:12199 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.159:3800 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.167:8979 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.168:41265 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.253:110 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.204.253:42899 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.13:45871 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.21:30876 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.25:14268 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.33:34977 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.48:10341 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.83:34616 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.99:61131 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.108:25308 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.120:32518 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.132:19994 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.141:19963 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.156:33968 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.166:30767 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.168:43023 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.205:26514 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.209:14503 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.211:24103 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.232:55726 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.238:28938 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.205.247:41222 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.206.18:41420 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.206.67:11797 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.206.67:33278 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.206.71:23589 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.206.72:34103 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.206.72:47910 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.206.148:5717 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.206.151:35142 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.206.152:41497 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.206.168:43189 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.206.182:12590 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.206.195:4970 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.206.200:54689 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.206.202:25223 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.206.218:34415 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.206.245:2340 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.206.245:33479 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.206.247:16788 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.5:38364 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.8:46810 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.23:61501 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.48:27829 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.51:22341 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.61:65136 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.82:462 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.119:49281 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.124:63011 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.130:46924 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.131:5030 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.135:21776 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.153:27750 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.160:57700 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.177:1513 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.179:61115 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.182:26510 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.184:44902 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.184:51213 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.187:7599 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.195:14611 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.234:60649 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.239:39681 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.246:47011 SYN_RECEIVED
TCP 10.10.10.12:443 187.111.207.254:3642 SYN_RECEIVED
TCP 10.10.10.12:444 10.10.10.12:7546 ESTABLISHED
...
Address the SYN flood problem
After all that, the solution seemed simple enough. I put in a firewall rule to block that whole IP Address range. This firewall rule does the trick, Well, sort-of. I’ll get to that in a few paragraphs.
0 0 DROP 0 -- enp2s0 * 187.111.192.0/20 0.0.0.0/0And a few minutes later, life went back to normal. Until a few minutes after that, when that SYN flood DDoS attack started again, this time from another IP Address range inside that same Brazilian internet service provider. I also blocked that range, but then a few minutes later, the SYN flood came right back.
Enough is enough. I composed and sent this email to Brazil.
From: Greg Scott
Sent: Friday, October 11, 2024 7:16 PM
To: 'noc@powertelecom.net.br' <noc@powertelecom.net.br>
Subject: Somebody is hijacking your bandwidth to launch DDOS attacks
Hi - I’m Greg Scott and I’m on the wrong end of a SYN flood DDOS attack coming from these IP Address ranges in your network. The ranges are:
187.111.192.0/20
187.62.64.0/22
Here is a small sample of what you’re blasting my way.
[root@infra2020-fw firewall-scripts]# date
Fri Oct 11 07:11:18 PM CDT 2024
[root@infra2020-fw firewall-scripts]# iptables -L -v -n | grep 187.111.192.0
505K 26M DROP 0 -- enp2s0 * 187.111.192.0/20 0.0.0.0/0
[root@infra2020-fw firewall-scripts]#
[root@infra2020-fw firewall-scripts]# date
Fri Oct 11 07:11:39 PM CDT 2024
[root@infra2020-fw firewall-scripts]# iptables -L -v -n | grep 187.111.192.0
510K 27M DROP 0 -- enp2s0 * 187.111.192.0/20 0.0.0.0/0
[root@infra2020-fw firewall-scripts]#
Please make it stop. My cell number is ******** (Blanked out for this blog post).
Thank you
- Greg Scott
Shortly after sending that email, the SYN flood stopped. I like to think I helped that Brazilian ISP address a vulnerability. But I found it mighty suspicious that systems all over its network attacked me.
Lessons
Good firewalls offer techniques to hypothetically slow SYN floods. Unfortunately, these are only marginally helpful. After I blocked the SYN flood hitting me, none of it passed through my firewall. This was good. But all of it still flooded into my firewall and brought my internet connection to a crawl. That was bad. The only real DDoS cure is, work with upstream bandwidth providers to block the flood before it hits. And upstream providers might need to work with their upstream providers. This means lots of players need to cooperate.
Maybe I’ll call my internet service provider and find out if they’re willing to help me the next time this happens. I’ll also send a link to this blog post to that Brazilian ISP.
A few weeks later – it’s really a reflection SYN Flood attack
When I first wrote this blog post, I thought my attacker was from Brazil. I was wrong. My attacker inserted Brazilian IP addresses into the packet headers to make it look like the attack came from Brazil. But in fact, Brazil was even more of a victim than me. This is a SYN flood reflection attack, meaning I reflect this flood to the ultimate victim. It works like this.
- My attacker sends me a SYN packet with forged source IP Address.
- I respond with a SYN+ACK to the forged address. That’s the reflection. The forged source address induces me to reflect my response to the forged address. I don’t know the real source Address.
- This attack floods the ultimate victim by using millions of intermediaries like me as reflection drones.
- On my own, I have no way to find my attacker.
See, “My DDoS attack: the rest of the story,” for the rest of the story.

Recent Comments