For more phishing samples, see my phishy email collection.
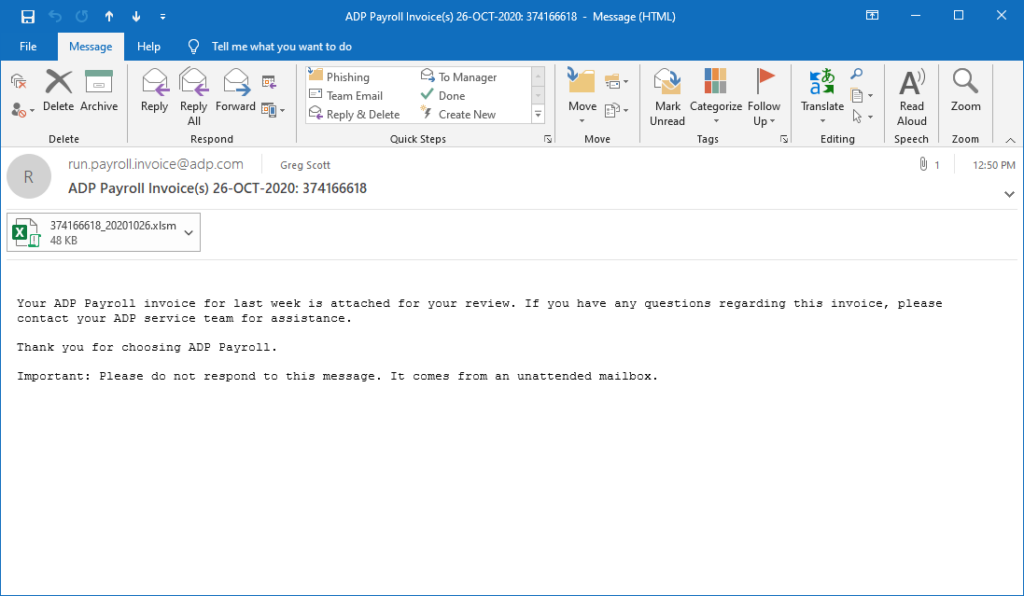
This is a great phishing attack, designed to look like a routine invoice. No doubt, the attached spreadsheet includes a nasty surprise. Don’t fall for it. I give this one an A-. Ya never know what you might find when chasing email headers. This one came from the US Department of Defense and routed through Armenia.
Details below the screenshot.
Relevant portion of the email header
To look at the email header in Outlook, click File…Properties. Email headers have a treasure-trove of routing and diagnostic information.
.
.
.
Received: from 178.160.250.142 by
mail2016.infrasupport.local (10.10.10.14) with Microsoft SMTP Server id
15.1.1531.3 via Frontend Transport; Mon, 26 Oct 2020 12:50:22 -0500
Received: from LYEIDOP.smtprelay.gslb.es.oneadp.com (LYEIDOP.smtprelay.gslb.es.oneadp.com
[26.110.198.75]) by with SMTP id
3fb06ys5gfgrutt.4.20201026215022; Mon, 26 Oct 2020 21:50:22 +0400
To: gregscott@infrasupportetc.com
Subject: ADP Payroll Invoice(s) 26-OCT-2020: 374166618
Message-ID: 43d115e0-897c-3b46-1ae5-@smtprelay.gslb.es.oneadp.com
Date: Mon, 26 Oct 2020 21:50:22 +0400
From: run.payroll.invoice@adp.com
.
.
.
This one claimed to start inside ADP and relay through an intermediate server. But a whois lookup on IP Address 26.110.198.75 shows it really came from the United States Department of Defense. Gulp – let that sink in.
Yep, Apparently, somebody compromised a government computer, forged a fake name to impersonate ADP, and used it to ensnare gullible businesses. Our tax dollars at work. Here is the entire whois output.
I generated this with the linux whois command. Whois information is also available by querying the whois website.
[root@www ~]# whois 26.110.198.75 [Querying whois.arin.net] [whois.arin.net] # ARIN WHOIS data and services are subject to the Terms of Use available at: https://www.arin.net/resources/registry/whois/tou/ # If you see inaccuracies in the results, please report at https://www.arin.net/resources/registry/whois/inaccuracy_reporting/ # Copyright 1997-2020, American Registry for Internet Numbers, Ltd. # NetRange: 26.0.0.0 - 26.255.255.255 CIDR: 26.0.0.0/8 NetName: DISANET26 NetHandle: NET-26-0-0-0-1 Parent: () NetType: Direct Allocation OriginAS: Organization: DoD Network Information Center (DNIC) RegDate: 1995-05-01 Updated: 2009-06-19 Ref: https://rdap.arin.net/registry/ip/26.0.0.0 OrgName: DoD Network Information Center OrgId: DNIC Address: 3990 E. Broad Street City: Columbus StateProv: OH PostalCode: 43218 Country: US RegDate: Updated: 2011-08-17 Ref: https://rdap.arin.net/registry/entity/DNIC OrgTechHandle: MIL-HSTMST-ARIN OrgTechName: Network DoD OrgTechPhone: +1-844-347-2457 OrgTechEmail: disa.columbus.ns.mbx.hostmaster-dod-nic@mail.mil OrgTechRef: https://rdap.arin.net/registry/entity/MIL-HSTMST-ARIN OrgTechHandle: REGIS10-ARIN OrgTechName: Registration OrgTechPhone: +1-844-347-2457 OrgTechEmail: disa.columbus.ns.mbx.arin-registrations@mail.mil OrgTechRef: https://rdap.arin.net/registry/entity/REGIS10-ARIN OrgAbuseHandle: REGIS10-ARIN OrgAbuseName: Registration OrgAbusePhone: +1-844-347-2457 OrgAbuseEmail: disa.columbus.ns.mbx.arin-registrations@mail.mil OrgAbuseRef: https://rdap.arin.net/registry/entity/REGIS10-ARIN # ARIN WHOIS data and services are subject to the Terms of Use available at: https://www.arin.net/resources/registry/whois/tou/ # If you see inaccuracies in the results, please report at https://www.arin.net/resources/registry/whois/inaccuracy_reporting/ # Copyright 1997-2020, American Registry for Internet Numbers, Ltd. # [root@www ~]#
What about the intermediate relay server? As long as we’ve gone to the trouble, may as well check it out too. First, a whois lookup for IP Address 178.160.250.142. This just keeps getting better. The intermediate relay server is in Armenia. Here is the complete whois output.
[root@www ~]# whois 178.160.250.142 [Querying whois.ripe.net] [whois.ripe.net] % This is the RIPE Database query service. % The objects are in RPSL format. % % The RIPE Database is subject to Terms and Conditions. % See http://www.ripe.net/db/support/db-terms-conditions.pdf % Note: this output has been filtered. % To receive output for a database update, use the "-B" flag. % Information related to '178.160.128.0 - 178.160.255.255' % Abuse contact for '178.160.128.0 - 178.160.255.255' is 'abuse@beeline.am' inetnum: 178.160.128.0 - 178.160.255.255 netname: AM-ARMENTEL-20100122 country: AM org: ORG-ATCh1-RIPE admin-c: ANOD1-RIPE tech-c: ANOD1-RIPE status: ALLOCATED PA mnt-by: RIPE-NCC-HM-MNT mnt-by: ARMENTEL-MNT mnt-routes: ARMENTEL-MNT created: 2010-01-22T15:00:00Z last-modified: 2016-09-22T11:29:34Z source: RIPE # Filtered organisation: ORG-ATCh1-RIPE org-name: VEON Armenia CJSC org-type: LIR address: 2 Aharonian street address: 0014 address: Yerevan address: ARMENIA phone: +37410289787 fax-no: +37410289770 abuse-c: AR14046-RIPE admin-c: AA5090-RIPE admin-c: AH5263-RIPE mnt-ref: ARMENTEL-MNT mnt-ref: RIPE-NCC-HM-MNT mnt-by: RIPE-NCC-HM-MNT mnt-by: ARMENTEL-MNT created: 2004-04-17T10:58:03Z last-modified: 2018-01-15T09:30:05Z source: RIPE # Filtered role: Armentel Network Operational Division role address: 24/1 Azatoutyan Ave. address: Yerevan 0014 address: Republic of Armenia abuse-mailbox: abuse@beeline.am admin-c: AA5090-RIPE tech-c: AA5090-RIPE nic-hdl: ANOD1-RIPE created: 2010-01-18T09:02:39Z last-modified: 2016-04-05T12:05:03Z mnt-by: RIPE-NCC-LOCKED-MNT source: RIPE # Filtered % Information related to '178.160.248.0/22AS12297' route: 178.160.248.0/22 descr: "VEON Armenia" CJSC origin: AS12297 mnt-by: ARMENTEL-MNT created: 2020-05-22T12:53:14Z last-modified: 2020-05-22T13:10:59Z source: RIPE % This query was served by the RIPE Database Query Service version 1.98 (ANGUS) [root@www ~]#

Trackbacks/Pingbacks