This spear-phishing attack came from my work email. Somebody tailored this especially for me. So now, I’m a VIP because I’m important enough to individually attack. Maybe I’ll puff out my chest and walk with extra spring in my steps.
For more phishing samples, see my phishy email collection.
More seriously, this is the best attack I’ve seen. Somebody impersonated Kenisha to get my attention. Which means the attackers did their homework to pick Kenisha and me as victims.
Details matter. Kenisha works in the corporate headquarters office in Raleigh, North Carolina. The 919 area code fits. The sender didn’t bother to impersonate Kenisha’s work email because the attacker knew spam filters would block it. Instead, they came up with a plausible reason why Kenisha would use another email address. The email header showed the email went through an outbound spam filter. It had nothing useful.
The whole thing works. Except…
It felt phishy. I didn’t know Kenisha until this email. Why would she want a private text message conversation outside of work?
Maybe I’m not such a VIP after all. If I start texting with the attacker, they’ll try to persuade me to give away other information. And if they gain enough tidbits from enough spear-phishing victims, maybe they’ll find a juicy attack target. Which means, I’m probably not the attack target. I’m a pawn in a larger attack.
So much for my ego.
Another A.
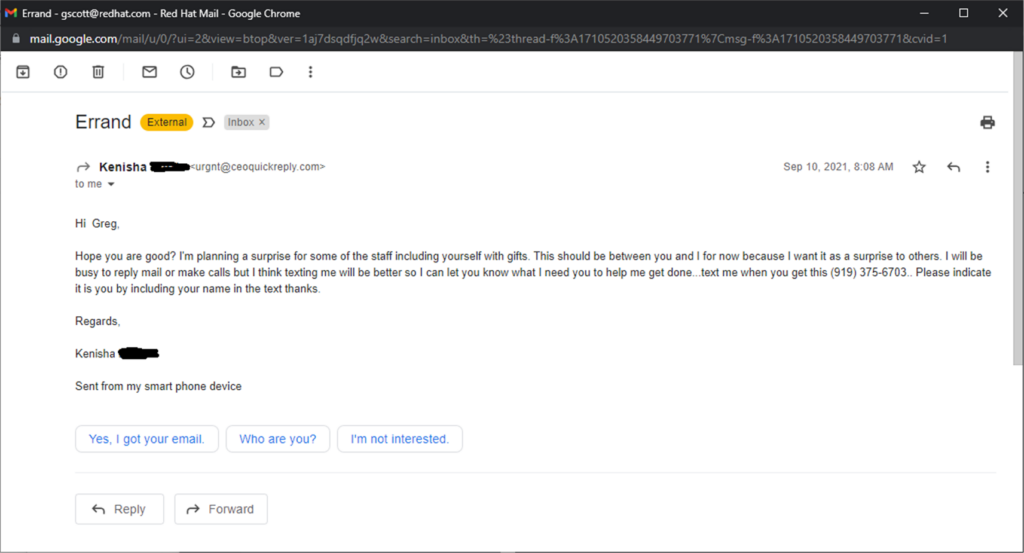

Definitely has that phishy smell. Also, grammatical errors like “Hope you are well?” set off my Red flags. Nice catch though, and thanks for informing the public to such nefariousness!
Thanks Greg! Took me a few days to get to comments.